Source: Anonymous
With COVID-19 well seeded in our daily lives where social distancing and limited outings were now commonplace, many of us were confronted with trying to vote in the 2020 Election. Many voters were torn at the thought of casting their 2020 Presidential vote in person. Many others, including service members, had no choice but to cast an absentee ballot. However, for those who were able to carry out their patriotic duty in-person, they would be unknowingly plagued with electronic ‘mishaps’ in key states that would raise eyebrows and cast doubt for some while creating unwanted ‘conspiracy theories’ for others during the 2020 Presidential Election.
As a high skill level Cybersecurity Firm that activity performs security research and responsibly discloses numerous zero-day discoveries each year and being a Cybersecurity Firm that performs large amounts of Penetration Testing Engagements, Software and Hardware Testing, Compliance Assessments and more wanted to do a little research on the issue and offer a professional opinion. We have extracted public information primarily in the form of published reports to look at the equipment and processes that are being utilized in the 2020 Election and present them to you. These discoveries are meant to help inform any voter in the United States, raise awareness, and lift the veil to get a better understanding of what is being utilized that has caused so much controversy. We maintain absolute neutrality and impartiality in our research and report only facts in this presentation. We will provide only our professional opinions and professional analysis of the data collected.
Many electronic voting platforms have been put forward as viable options to the American Election System for review and use in the United States Elections. However, 3 vendors are the primary suppliers of the platforms which are: Dominion Voting Systems, American Hart InterCivic, and the American Election Systems & Software (ES&S). These systems undergo routine and constant testing of their policies, hardware, software, and source code. The U.S. Election Assistance Commission (EAC), established by the Help America Vote Act (HAVA), develops Voluntary Voting System Guidelines (VVSG). These guidelines rely on the National Institute of Standards and Technology (NIST) for the technical guidelines.
Testing and Certification of the Voting Systems differ a bit for each state. When we focus on the states that have found themselves in the news the most (Pennsylvania, Georgia, North Carolina, Michigan, Wisconsin, Arizona, Nevada), we find they all have different requirements for testing:
Nevada – requires testing to federal standards
Georgia – requires full federal certification
North Carolina – requires full federal certification
Pennsylvania – requires testing be performed by a federally accredited laboratory
Michigan – requires testing be performed by a federally accredited laboratory
Wisconsin – requires testing be performed by a federally accredited laboratory Arizona – requires testing be performed by a federally accredited laboratory
Some states like Kansas only comply with compliance, while some like Nebraska, New Hampshire, New Jersey have no federal testing or certification requirements at all.
With such vast requirement differences and standards of testing or none at all, it is difficult (and in some cases impossible) to identify exactly how each state is verifying and validating correct system functionality as well as resistance to a cyberattack of the Voting Systems. Later in this paper, we identify some publicly available information pertaining to the testing and concerns of some Voting Systems in the span of the past 15 years.
The word ‘glitch’ reported on several media outlets during the 2020 Presidential Election. Anytime we hear the word ‘glitch’, we must take a very close look at the issue and validate whether the ‘glitch’ is real, then test to validate if it can be duplicated. If it can in-fact be duplicated, we then need to look at the scenario that caused the glitch. Knowing there are multiple vendors that provide equipment for US Elections, a ‘glitch’ must be fully investigated and reported on using the precise setup and conditions where it was discovered so that it can be accurately duplicated and recreated. The same scenario should then be investigated on any other ‘similar’ platform to test if the ‘glitch’ can be duplicated on those systems as well.
Live testing is never an ideal scenario, however, it should be expected and planned for. Being able to quickly determine if an issue is isolated or if it propagates over one, some, many, or all similar platforms can be the difference between responsibility and controversy. Full Transparency in these situations is critical.
What we have found during our research is a common theme played out time and time again. What we have found is authorized vendors are permitted to test the Voting Equipment and Platforms. However, what we do not find is information on if the source-code is properly tested if it is tested at all. The lack of transparency has led to controversially scenarios and concerns. Some examples of scenarios causing the greatest concern whereby technical evidence to the contrary cannot be found include:
- Can votes be switched?
- Can votes be automatically switched with software?
- Can votes be removed?
- Can votes be removed automatically with software?
- Can invalid votes be cast for a given party?
- Can invalid votes be cast for a given party automatically?
- Can bulk votes be introduced for a given party?
- Can bulk votes be removed for a given party?
- Can access be gained to the voting system remotely and information changed?
Important to Understand
CISA has reported there was no indication of fraud or mishaps in the below publication.
However, this assessment is based on flawed information and a misleading process. The process cited is the Election Assistance Commission (EAC) compliance report which focuses on the calibration of the voting machines and a limited look at the voting software. The type of testing applied and methodology used does not appear to factor or test critical security elements in a meaningful way or thoroughly examine the actual source code and cannot with any certainty be used to substantiate the security posture of the voting system.
Below is the link to the Pro V& V report that documents the type of testing performed on the Dominion Democracy Suite 5.5c under the EAC evaluation process.
https://www.eac.gov/voting-equipment/democracy-suite-55-c
The report document in Analysis Item 8 is the only actual Red Team / Penetration Test of the Dominion Democracy Suite that we could locate in the public domain. The report definitively demonstrates the Penetration Testing team having discovered and exploited many significant vulnerabilities with the Dominion Democracy Suite leaving significant concerns about the voting platform’s security and resistance to fraud and unauthorized manipulation. While this report was published in 2014, continued reports from State evaluations (although not penetration tests) show a trend of continued security failures.
Analysis of Discovered Reports and Documents
Our Analysis on Published Documents and Reports Relating to Dominion Voting Machines (many of discovered reports are heavily buried and likely not known to the host but are indexed by Google and publicly available nevertheless):
1. MAJOR Findings Significantly Downplayed – The following link is the Test Report for the Dominion Democracy Suite 5.2 Source Code performed by SLI Compliance in Wheat Ridge Colorado – this report details no major findings were discovered, which when the entirely of the report is taken into context is not accurate. There are indeed major findings, but they wrap them with only ‘an insider’ would be the one to take advantage of discovered vulnerabilities and the report does not detail the findings. These are serious vulnerabilities that are commonly exploited by attackers such as SQL Injections, memcopy, strcopy, and more. Best practices and a thorough testing approach would be to test these in an ‘assumed breach’ scenario and detail exactly what would be required to exploit them. Immediately following this information would be a thorough analysis of what the consequences would be if exploited. As it stands in the published report, this is a major gap that should be examined as soon as possible.
https://www.google.com/url?q=https://votingsystems.cdn.sos.ca.gov/vendors/dominion/ds52- sc.pdf&sa=D&source=hangouts&ust=1605278658967000&usg=AFQjCNGRQYJJuOjcigVwR6P4sSE LzfRMPw
2. MAJOR Findings Significantly Downplayed – The following link is the Dominion Democracy Suite 4.14-A.1 Voting System with Adjudication Version 2.4 ‘Source Code Review’ results performed by Asec & Freeman, Craft, McGregor Group on 11/14/2014. ALL findings in this report are reported as ‘Low’ including the use of SHA-1 for key generation, code exceptions that can cause a denial of service and potentially access to the platform, and the potential for buffer overflow exploit. Many of these should be classified as a high criticality vulnerability and from experience, we regularly successfully exploit the same type of vulnerabilities on other systems. Further, the report contains only 12 pages which beg questions as to how thorough the testing was.
https://www.google.com/url?q=https://verifiedvoting.org/wp- content/uploads/2020/08/adjudication.pdf&sa=D&source=hangouts&ust=1605278658967000& usg=AFQjCNERb8F65NdqjYuC-2CJfldk0vTygQ
3. Significant Concerns with Voting System Not Addressed and System was not Approved for Future Releases – The following link is the Dominion Democracy Suite Release 4.14.37 Version 2 Voting System Qualification Test Report prepared by The Bureau of Voting Systems Certification (BVSC) Florida Department of State Division of Elections in January 2020. While the system presented passed inspection, the Bureau did not recommend the approval of any future releases for this voting system unless the issues in the Continuous Improvements/Recommendations section were addressed and no longer an issue, including unexpected ICP system shutdown and ‘confusing’ data output.
https://www.google.com/url?q=https://dos.myflorida.com/media/702601/dominion- democracy-suite-release-41437-version-2-test- report.pdf&sa=D&source=hangouts&ust=1605278658967000&usg=AFQjCNEMrQGySUhEZV7Wg CTJGOqVCig9PQ
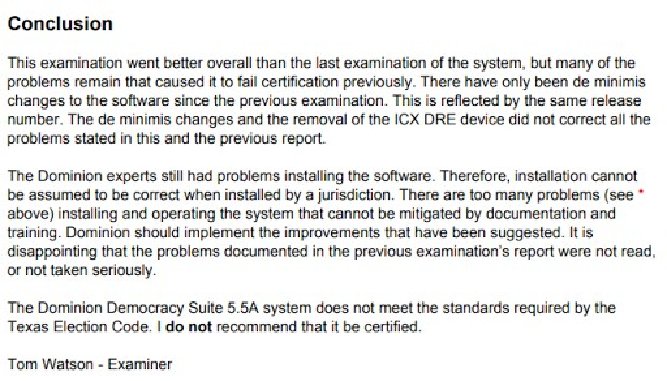
4. Voting System Failed Texas Certification and Denied for Use in Texas Elections – The following link is the Report of review of Dominion Voting Systems Democracy Suite 5.5-A by The State of Texas Elections Division on October 2-3, 2019. The findings in this report include ‘multiple hardware and software issues that preclude the Office of the Texas Secretary of State from determining the Democracy Suite 5.5-A system satisfies each of the voting-system requirements set forth in the Texas Election Code. Specifically, the examiner reports raise concerns about whether the Democracy Suite 5.5-A system is suitable for its intended purpose; operates efficiently and accurately; and is safe from fraudulent or unauthorized manipulation.
Therefore, the Democracy Suite 5.5-A system and corresponding hardware devices to not meet the standards for certification prescribed by Section 122.001 of the Texas Election Code’ The Democracy Suite 5.5-A system was thus denied certification for use in Texas Elections, signed by Deputy Secretary of State, Jose A. Esparaza on January 24th, 2020.
https://www.google.com/url?q=https://www.sos.texas.gov/elections/forms/sysexam/dominion
-d-suite-5.5- a.pdf&sa=D&source=hangouts&ust=1605278658967000&usg=AFQjCNG6Ey27tBkMIt6COPqsdD wpXKhR7w
Here is the link to Section 122.001 of the Texas Election Code:
https://statutes.capitol.texas.gov/Docs/EL/htm/EL.122.htm#122
It is very short and specifies the following:
Sec. 122.001. VOTING SYSTEM STANDARDS.
- A voting system may not be used in an election unless the system:
- preserves the secrecy of the ballot;
- is suitable for the purpose for which it is intended;
- operates safely, efficiently, and accurately and complies with the voting system standards adopted by the Election Assistance Commission;
- is safe from fraudulent or unauthorized manipulation;
- permits voting on all offices and measures to be voted on at the election;
- prevents counting votes on offices and measures on which the voter is not entitled to vote;
- prevents counting votes by the same voter for more than one candidate for the same office or, in elections in which a voter is entitled to vote for more than one candidate for the same office, prevents counting votes for more than the number of candidates for which the voter is entitled to vote;2020.
- prevents counting a vote on the same office or measure more than once;
- permits write-in voting; and
- is capable of providing records from which the operation of the voting system may be
- Repealed by Acts 2017, 85th Leg., S., Ch. 404 (H.B. 25), Sec. 8, eff. September 1,
- The secretary of state may prescribe additional standards for voting systems consistent with this The standards may apply to particular kinds of voting systems, to particular elements comprising a voting system, including operation procedures, or to voting systems generally.
- Effective January 1, 2006, a voting system may not be used in an election if the system uses:
- mechanical voting machines; or
- a punch-card ballot or a similar form of a tabulating card.
- For an election for federal office in which a state or federal court order has extended the time for voting beyond the time allowed by Subchapter B, Chapter 41, a voting system must provide a separate count of the votes cast after the time allowed by that
5. Voting System Determined to have a High Risk of an Insecure Configuration when Installed, even when Installed by the Vendor – In response to the Voting System failing TX certification, the following link is a ‘concern’ by Mr. Brandon T. Hurley. He begins by stating he is a newly appointed voting systems examiner under Texas Election code 122.035 and points out many problems and concerns he has with the Democracy Suite 5.5-A platform including: Many Security features are not automatic, rather they rely on the end-user following instructions, the system is difficult to build and implement and caused issues even for the Dominion installers, the system can be without question connected to external communication networks and can only be avoided if the end-user takes proper precautions to prevent such connections, thus his recommendation was for non-certification and non-use in Texas Elections:
https://www.google.com/url?q=https://www.sos.texas.gov/elections/forms/sysexam/oct2019- hurley.pdf&sa=D&source=hangouts&ust=1605278658967000&usg=AFQjCNFIV7uZkXiMD5v667_ DE4AVklAeAA
6. Voting System Again Determined to Fail Texas Certification Requirements – The following link is a summary of all of the findings by Tom Watson another Texas certified voting systems examiner. His report details many concerns including: problems installing the Dominion Software which led to software failures; the difficulty verifying the integrity of the software will likely result in many jurisdictions that simply decide not configure the product in a secure manner before the elections; Party affiliations were missing from candidates; Ethernet ports were active; system crashes which would cause adjudication to be redone; firewalls are not configured as part of hardening and left to each jurisdiction; and much more:
https://www.google.com/url?q=https://www.sos.texas.gov/elections/forms/sysexam/oct2019- watson.pdf&sa=D&source=hangouts&ust=1605278658967000&usg=AFQjCNEBRxxb5g- ifwBTOU0Gq8aYxQywkQ
The below link is to yet another failed certification in 2019:
https://voterga.files.wordpress.com/2019/08/texas-sos-rejection-of-dominion.pdf
7. Dominion Vulnerability Disclosure Program Only Factors Peripheral Elements – The following link is to the Dominion Voting Coordinated Vulnerability Disclosure Program. This Program encourages transparency and permits the public and 3rd parties to report potential vulnerabilities to Dominion. However, this appears to only be for vulnerabilities related to the Dominion hosting platform, and not for the source code that actually processes the data. Our research indicates that only certified election voting equipment testers can access the actual code for testing but even that appears to be restricted to peripheral code (and not source code). Without testing the actual source code via a skilled penetration testing resource and mimicking real-world operations, it is impossible to assess if the code is secure from manipulation.
https://www.google.com/url?q=https://www.dominionvoting.com/coordinated-vulnerability-
disclosure- policy/&sa=D&source=hangouts&ust=1605278658967000&usg=AFQjCNGI5NISUGjbcB3RmT8W e6q8V_z3BQ
8. Voting System has History of Being Implemented with Significant Security Flaws – The following is the link to the Red Team Test Report for the Dominion Democracy Suite 4.14-A and4.14.A.1 w/Adjudication 2.4. This test report from Freeman, Craft, McGregor Group on November 18th, 2014 details the test methods and findings for the systems. These findings include: System/Hardware failures; Users have Administrative permissions; Display failures; No centralized GPO configuration management; Missing Windows Updates; Anti-Virus was in evaluation mode; Missing Trust Relationships; Encryption Keys could be and were recovered; User credentials recovered from memory; Flash drive doors could be opened and seals removed; ballot scanner box door could be opened during an election and ballots added or removed without detection, and much more:
https://www.google.com/url?q=https://verifiedvoting.org/wp-content/uploads/2020/08/red- team-support.pdf&sa=D&source=hangouts&ust=1605278658967000&usg=AFQjCNGjITVe- qTdzK3Bf83PhsDeD9w0Gw